Threat model
Threat modeling is a process by which potential threats can be identified, enumerated, and prioritized – all from a hypothetical attacker’s point of view. The purpose of threat modeling is to provide defenders with a systematic analysis of the probable attacker’s profile, the most likely attack vectors, and the assets most desired by an attacker. Threat modeling answers the questions “Where are the high-value assets?” “Where am I most vulnerable to attack?” “What are the most relevant threats?” “Is there an attack vector that might go unnoticed?”
Conceptually, most people incorporate some form of threat modeling in their daily life and don’t even realize it. Commuters use threat modeling to consider what might go wrong during the morning drive to work and to take preemptive action to avoid possible accidents. Children engage in threat modeling when determining the best path toward an intended goal while avoiding the playground bully. In a more formal sense, threat modeling has been used to prioritize military defensive preparations since antiquity.
Evolution of IT-Based Threat Modeling
Shortly after shared computing made its debut in the early 1960s individuals began seeking ways to exploit security vulnerabilities for personal gain.[1] As a result, engineers and computer scientists soon began developing threat modeling concepts for information technology systems.
Early IT-based threat modeling methodologies were based on the concept of architectural patterns[2] first presented by Christopher Alexander in 1977. In 1988 Robert Barnard developed and successfully applied the first profile for an IT-system attacker.
In 1994, Edward Amoroso put forth the concept of a “threat tree” in his book, “Fundamentals of Computer Security Technology.[3]” The concept of a threat tree was based on decision tree diagrams. Threat trees graphically represent how a potential threat to an IT system can be exploited.
Independently, similar work was conducted by the NSA and DARPA on a structured graphical representation of how specific attacks against IT-systems could be executed. The resulting representation were called “attack trees.” In 1998 Bruce Schneier published his analysis of cyber risks utilizing attack trees in his paper entitled “Toward a Secure System Engineering Methodology.[4]” The paper proved to be a seminal contribution in the evolution of threat modeling for IT-systems. In Schneier’s analysis, the attacker’s goal is represented as a “root node,” with the potential means of reaching the goal represented as “leaf nodes.” Utilizing the attack tree in this way allowed cybersecurity professionals to systematically consider multiple attack vectors against any defined target.
In 1999, Microsoft cybersecurity professionals Loren Kohnfelder and Praerit Gard applied Schneier’s attack tree analysis to develop a methodical means to consider potential attacks relevant to the Microsoft Windows development environment. The resultant STRIDE[5] threat model (STRIDE is an acronym for Spoofing identity, Tampering with data, Repudiation, Information disclosure, Denial of service, Elevation of privilege) required security professionals to systematically determine how a potential attacker could utilize any threat categorized by the STRIDE acronym at each node of a Schneier-type attack tree.
In 2003, OCTAVE[6] (Operationally Critical Threat, Asset, and Vulnerability Evaluation) method, a risk-based assessment threat modeling methodology, was first introduced with a primary focus on organizational risk management.
In 2004, Frank Swiderski and Window Snyder wrote “Threat Modeling,” by Microsoft press. In it they developed the concept of using threat models to create secure applications.
Threat Modeling Methodologies for IT Purposes
Conceptually a threat modeling practice flows from a methodology. Numerous threat modeling methodologies are available for implementation. Based on volume of published online content, the four methodologies discussed below are the most well known.
STRIDE Methodology
The STRIDE approach to threat modeling was introduced in 1999 at Microsoft, providing a mnemonic for developers to find 'threats to our products' [7] . STRIDE, Patterns and Practices, and Asset/entry point were amongst the threat modeling approaches developed and published by Microsoft. References to "the" Microsoft methodology commonly mean STRIDE.
P.A.S.T.A.
The Process for Attack Simulation and Threat Analysis (PASTA) is a seven-step, risk-centric methodology.[8] It provides a seven-step process for aligning business objectives and technical requirements, taking into account compliance issues and business analysis. The intent of the method is to provide a dynamic threat identification, enumeration, and scoring process. Once the threat model is completed security subject matter experts develop a detailed analysis of the identified threats. Finally, appropriate security controls can be enumerated. This methodology is intended to provide an attacker-centric view of the application and infrastructure from which defenders can develop an asset-centric mitigation strategy.
Trike
The focus of the Trike methodology[9] is using threat models as a risk-management tool. Within this framework, threat models are used to satisfy the security auditing process. Threat models are based on a “requirements model.” The requirements model establishes the stakeholder-defined “acceptable” level of risk assigned to each asset class. Analysis of the requirements model yields a threat model form which threats are enumerated and assigned risk values. The completed threat model is used to construct a risk model based on asset, roles, actions, and calculated risk exposure.
VAST
VAST is an acronym for Visual, Agile, and Simple Threat modeling.[10] The underlying principle of this methodology is the necessity of scaling the threat modeling process across the infrastructure and entire SDLC, and integrating it seamlessly into an Agile software development methodology. The methodology seeks to provide actionable outputs for the unique needs of various stakeholders: application architects and developers, cybersecurity personnel, and senior executives. The methodology provides a unique application and infrastructure visualization scheme such that the creation and use of threat models do not require specific security subject matter expertise.
Generally Accepted IT Threat Modeling Processes
All IT-related threat modeling processes start with creating a visual representation of the application and / or infrastructure being analyzed. The application / infrastructure is decomposed into various elements to aid in the analysis. Once completed, the visual representation is used to identify and enumerate potential threats. Further analysis of the model regarding risks associated with identified threats, prioritization of threats, and enumeration of the appropriate mitigating controls depends on the methodological basis for the threat model process being utilized.
Visual Representations based on Data Flow Diagrams
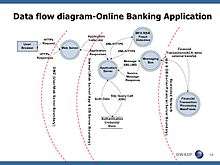
The Microsoft methodology, PASTA, and Trike each develop a visual representation of the application-infrastructure utilizing data flow diagrams (DFD).[11] DFDs were developed in the 1970s as tool for system engineers to communicate, on a high level, how an application caused data to flow, be stored, and manipulated by the infrastructure upon which the application runs. Traditionally, DFDs utilize only four unique symbols: data flows, data stores, processes, and interactors. In the early 2000s, an additional symbol, trust boundaries, were added to allow DFDs to be utilized for threat modeling.
Once the application-infrastructure system is decomposed into its five elements, security experts consider each identified threat entry point against all known threat categories. Once the potential threats are identified, mitigating security controls can be enumerated or additional analysis can be performed.
Visual Representations based on Process Flow Diagrams
The VAST methodology distinguished between application threat models (ATM) and operational or infrastructure threat models (OTM).[12]
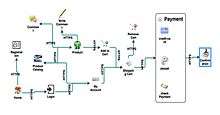
ATMs are built with process flow diagrams (PFD).[11] PFDs were developed in 2011 as a tool to allow Agile software development teams to create threat models based on the application design process. Applications are decomposed into their various features or use cases. Each feature is described in terms of the widgets or code building blocks required to build that feature. Features are then connected by communication protocols. The resulting visualization is a map of how a user moves through the various features of an application.
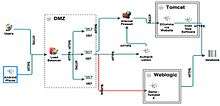
OTMs are built with end-to-end data flow diagrams very similar to traditional DFDs. End to end data flow diagrams decompose an IT system into its various independent, grouped, and shared components. Each component is described in terms of specific attributes. Components are then connected by communication pathways and protocols.
Once the ATM or OTM is constructed, the methodology specifies how potential threats are identified, enumerated, prioritized, and associated with their relevant risks and mitigating security controls.
Threat Modeling Tools
There are currently five tools available for organizational threat modeling:
- Microsoft offers a free threat modeling tool – the SDL Threat Modeling Tool.[13] This tool utilizes the Microsoft threat modeling methodology, is DFD-based, and identifies threats based on the STRIDE threat classification scheme. It is intended primarily for software development.
- Microsoft’s other free threat modeling tool – the Threat Modeling Tool.[14] This tool also utilizes the Microsoft threat modeling methodology, is DFD-based, and identifies threats based on the STRIDE threat classification scheme. It is intended primarily for general use.
- MyAppSecurity offers the first commercially available threat modeling tool - ThreatModeler[15] It utilizes the VAST methodology, is PFD-based, and identifies threats based on a customizable comprehensive threat library.[16] It is intended for collaborative use across all organizational stakeholders.
- Irius Risk offers both a community and a commercial version of the tool. This tool focus on the creation and maintenance of a live Threat Model trough all the SDLC. It drives the process by using fully customizable questionnaires and Risk Pattern Libraries and connects with other several different tools (OWASP ZAP, BDD-Security, Threadfix...) to empower automation.[17]
- foreseeti offers a commercial threat modeling tool – securiCAD. This tool focuses on threat modeling of IT infrastructures using a CAD-based approach where assets are automatically or manually placed on a drawing pane. By encapsulating complex attack trees within generalizable assets (like hosts, dataflows, firewalls, and IDS), securiCAD makes threat modeling accessible also for non-experts. By attaching an Attacker to different attack steps on available Assets, different scenarios can be simulated and analyzed. It is intended for company cyber security management, from CISO to security engineer to IT technician.[18] The further development of securiCAD is currently a part of the EU-funded project CyberWiz.[19] An article (in German) about CyberWiz containing some insights in the functionality of securiCAD has been published in the expert portal "Informatik aktuell".[20]
References
- ↑ McMillan, Robert (2012). "The World's First Computer Password? It Was Useless Too". Wired Business.
- ↑ Shostack, Adam (2014). "Threat Modeling: Designing for Security". John Wiley & Sons Inc: Indianapolis.
- ↑ Amoroso, Edward G (1994). "Fundamentals of Computer Security Technology". AT&T Bell Labs. Prentice-Hall: Upper Saddle River.
- ↑ Schneier, Bruce; et al. (1998). "Toward A Secure System Engineering Methodology" (PDF). National Security Agency: Washington.
- ↑ "The STRIDE Threat Mode". Microsoft. 2016.
- ↑ Alberts, Christopher (2003). "Introduction to the OCTAVE® Approach" (PDF). Software Engineering Institute, Carnegie Mellon: Pitsburg.
- ↑ Kohnfelder, Loren; Garg, Praerit. "Threats to Our Products". Microsoft. Retrieved 20 September 2016.
- ↑ Ucedavélez, Tony and Marco M. Morana (2015). "Risk Centric Threat Modeling: Process for Attack Simulation and Threat Analysis". John Wiley & Sons: Hobekin.
- ↑ Eddington, Michael, Brenda Larcom, and Eleanor Saitta (2005). "Trike v1 Methodology Document". Octotrike.org.
- ↑ Agarwal, Anurag “Archie,” etal. VAST Methodology: Visual, Agile, and Simple Threat Modeling. Various Interviews. Transformational Opportunities: Prescott Valley. 2016
- 1 2 Agarwal, Anurag "Archie" (2016). "Threat Modeling – Data Flow Diagram vs Process Flow Diagram". ThreatModeler.com.
- ↑ Agarwal, Anurag "Archie" (2016). "Application Threat Modeling vs Operational Threat Modeling". ThreatModeler.com.
- ↑ "SDL Threat Modeling Tool". Microsoft. 2016.
- ↑ "What's New with Microsoft Threat Modeling Tool 2016". Microsoft Secure Blog. Microsoft. 2015.
- ↑ "ThreatModeler Home". ThreatModeler.
- ↑ Agarwal, Anurag “Archie,” etal. Comprehensive Threat Library. Various Interviews. Transformational Opportunities: Prescott Valley. 2016
- ↑ "Irius Risk Risk Management Tool". Continuum Security. 2016.
- ↑ "Forerunners in cyber security threat modeling and proactive risk managment". foreseeti. 2016.
- ↑ "Website for the CyberWiz project".
- ↑ "CyberWiz - ein EU-Projekt zum schutz kritischer Infrastrukturen/". www.informatik-aktuell.de. Alkmene Verlag. 2016.