Syskey
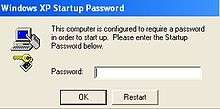
Syskey is a utility that encrypts the hashed password information in a SAM database in a Windows system using a 128-bit RC4 encryption key that, by default, is stored in the Windows registry. Syskey can optionally be configured to require the user to enter the key at boot time as a startup password or load it on removable storage media (e.g., USB flash drive).
Syskey was introduced with Windows NT 4.0 SP3.[1] It was meant to protect against offline password cracking attacks by preventing the possessor of an unauthorised copy of the SAM from extracting useful information from it.[1] However, these days the feature is being misused by scammers to lock naïve victims out of their own computers and so coerce them into paying a ransom.
Early vulnerability
In December 1999, a security team from BindView found a security hole in Syskey that indicated that a certain form of offline cryptanalytic attack is possible, making a brute force attack appear to be possible.[1] Microsoft later issued a fix for the problem (dubbed the "Syskey Bug").[2] The bug affected both Windows NT and pre-RC3 versions of Windows 2000.[1]
Malicious use
In what has been called the technical support scam, scammers claiming to represent Microsoft, Windows, Google, the FBI, or another group attempt to extort money from unsophisticated computer users, usually over the telephone. Using various social engineering techniques and pretexts (e.g., claiming that the victims' computers are infected with a virus, contain illicit content, or are about to fail due to "serious" errors that are in fact normal), scammers often try to fool victims into believing that their computers are in need of support or maintenance which the caller will provide on payment. If the direct approach fails, the scamming party will invoke the syskey command and configure a password known only to them, thereby locking the victim out of their own system after the computer is rebooted.[3][4]
See also
References
- 1 2 3 4 Sabin, Todd (December 16, 1999). "bindview.syskey.txt". Packet Storm. Retrieved July 1, 2016.
- ↑ Khanse, Anand (March 9, 2012). "Use SysKey Utility to lock Windows computer using USB stick". The Windows Club. Retrieved July 1, 2016.
- ↑ Woodchip computers:Have you been caught by the "I am Windows Support" scam?
- ↑ http://www.smh.com.au/it-pro/security-it/tech-support-company-with-workers-in-india-claims-its-good-name-being-ruined-by-scammers-20141116-11o361.html
- This article is based on material taken from the Free On-line Dictionary of Computing prior to 1 November 2008 and incorporated under the "relicensing" terms of the GFDL, version 1.3 or later.
External links
- How to use the SysKey utility to secure the Windows Security Accounts Manager database
- Enable Syskey To Protect Windows Against Local Password Cracking